Identifying and safeguarding pii knowledge check – In the digital age, where data is king, protecting personally identifiable information (PII) has become paramount. This comprehensive knowledge check delves into the intricacies of identifying and safeguarding PII, providing a roadmap for organizations to navigate the complexities of data privacy and compliance.
As the world becomes increasingly interconnected, understanding the methods for identifying PII, implementing robust safeguarding strategies, and staying abreast of regulatory considerations is essential for organizations to protect sensitive information and maintain customer trust.
1. Introduction to PII and its Importance: Identifying And Safeguarding Pii Knowledge Check
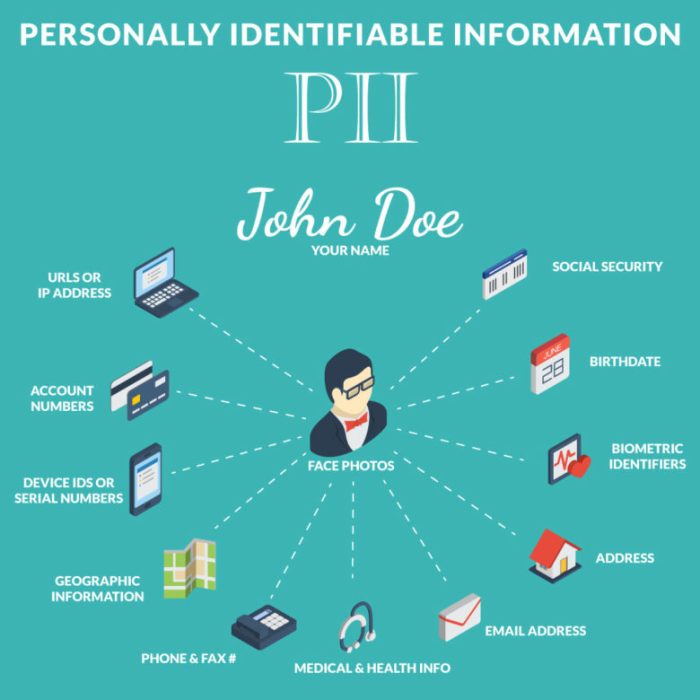
Personally identifiable information (PII)refers to any data that can be used to identify an individual. This includes information such as name, address, Social Security number, and biometric data. PII is essential for many business processes, but it also poses significant risks to privacy if not properly protected.
The legal and ethical implications of safeguarding PII are significant. In many jurisdictions, there are laws that require organizations to protect PII from unauthorized access and disclosure. In addition, there are ethical concerns about the potential misuse of PII for identity theft, fraud, or other harmful purposes.
PII breaches can have devastating consequences for both individuals and organizations. For individuals, PII breaches can lead to identity theft, financial loss, and reputational damage. For organizations, PII breaches can result in fines, lawsuits, and loss of customer trust.
2. Methods for Identifying PII
There are a variety of techniques that can be used to identify PII in structured and unstructured data. These techniques include:
- Data dictionaries:Data dictionaries are lists of fields and their corresponding data types. They can be used to identify PII fields by their data type (e.g., Social Security number, email address).
- Regular expressions:Regular expressions are patterns that can be used to identify specific types of data. For example, a regular expression can be used to identify all email addresses in a text document.
- Natural language processing (NLP):NLP is a field of artificial intelligence that deals with the understanding of human language. NLP techniques can be used to identify PII by its context. For example, an NLP algorithm can be used to identify a person’s name in a sentence by its relationship to other words in the sentence.
There are a number of tools and technologies that can be used to identify PII. These tools include:
- PII scanners:PII scanners are software programs that can scan data for PII. They can be used to identify PII in both structured and unstructured data.
- Data classification tools:Data classification tools can be used to classify data according to its sensitivity. This can help organizations to identify PII and other sensitive data that needs to be protected.
- Privacy dashboards:Privacy dashboards provide organizations with a centralized view of their PII data. This can help organizations to track their PII risks and to identify areas where they need to improve their PII protection measures.
3. Strategies for Safeguarding PII
There are a number of best practices that organizations can follow to protect PII from unauthorized access, disclosure, and misuse. These best practices include:
- Encryption:Encryption is the process of converting data into a format that cannot be read without a key. Encryption can be used to protect PII at rest (e.g., in a database) and in transit (e.g., over a network).
- Tokenization:Tokenization is the process of replacing PII with a unique identifier (token). Tokens can be used to protect PII from unauthorized access and disclosure. For example, a token can be used to replace a Social Security number in a database.
- Anonymization:Anonymization is the process of removing or modifying PII so that it cannot be used to identify an individual. Anonymization can be used to protect PII from unauthorized access and disclosure. For example, a person’s name can be anonymized by replacing it with a pseudonym.
In addition to these technical measures, organizations can also implement data governance and security policies to protect PII. These policies should define the roles and responsibilities for PII protection, and they should Artikel the procedures that must be followed to protect PII.
4. Regulatory and Compliance Considerations
There are a number of laws and regulations that govern the protection of PII. These laws and regulations vary from country to country, but they generally require organizations to protect PII from unauthorized access, disclosure, and misuse.
Some of the most important laws and regulations governing the protection of PII include:
- The General Data Protection Regulation (GDPR):The GDPR is a European Union law that protects the personal data of EU citizens. The GDPR requires organizations to implement a number of measures to protect PII, including encryption, tokenization, and anonymization.
- The California Consumer Privacy Act (CCPA):The CCPA is a California law that protects the personal data of California residents. The CCPA requires organizations to provide consumers with certain rights, including the right to know what PII is being collected about them, the right to delete their PII, and the right to opt out of the sale of their PII.
Organizations that handle PII should be aware of the laws and regulations that apply to them. They should also implement compliance strategies to ensure that they are in compliance with these laws and regulations.
5. Emerging Trends and Challenges, Identifying and safeguarding pii knowledge check
There are a number of emerging technologies that are having a significant impact on PII protection. These technologies include:
- Cloud computing:Cloud computing is the delivery of computing services over the Internet. Cloud computing can make it easier for organizations to store and process PII, but it also introduces new security risks.
- Big data:Big data refers to the large and complex data sets that are being generated by businesses and other organizations. Big data can make it difficult for organizations to identify and protect PII.
- The Internet of Things (IoT):The IoT refers to the network of physical devices that are connected to the Internet. The IoT can make it easier for organizations to collect PII, but it also introduces new security risks.
Organizations that handle PII need to be aware of the emerging technologies that are having an impact on PII protection. They need to implement strategies to address the security risks that these technologies introduce.
FAQ Corner
What is the significance of safeguarding PII?
Safeguarding PII is crucial for protecting individuals’ privacy, preventing identity theft and fraud, and maintaining customer trust.
How can organizations identify PII effectively?
Organizations can employ data dictionaries, regular expressions, and natural language processing tools to identify PII in structured and unstructured data.
What are the best practices for safeguarding PII?
Encryption, tokenization, and anonymization are essential techniques for protecting PII from unauthorized access and misuse.